The Hidden Risks Reshaping Supply Chain Security
Introduction to Modern Supply Chain Security
The world’s supply chains have evolved into interconnected, global systems that move goods at lightning speed. But as these networks grow more advanced, they also become more vulnerable.
Today’s supply chains face risks that are often unseen, unmanaged, and potentially devastating. From cyber threats to unpredictable political shifts, the challenges continue to reshape how businesses protect their operations.
Why Supply Chains Are More Vulnerable Today
Globalization and Complex Networks
Global supply networks now span dozens of countries and hundreds of suppliers. While this creates efficiency, it also increases exposure.
A single weak link—perhaps a small manufacturer in another region—can disrupt the entire chain.
Increased Dependency on Digital Systems
Businesses rely heavily on software, tracking systems, and automation. While technology speeds up processes, it also opens the door to hackers and system failures.
Emerging Threats in Supply Chain Management
Cybersecurity Challenges
Cyber risks are among the biggest threats today.
Ransomware Attacks on Logistics
Ports, shipping companies, and logistics centers have become prime targets. A single attack can halt operations, delay shipments, and cost millions.
Data Breaches and Information Theft
Cybercriminals can steal sensitive data such as supplier contacts, pricing, contracts, and shipment routes—putting companies at a strategic disadvantage.
Physical Security Risks
Theft and Cargo Tampering
Despite digital advances, old-fashioned theft is still a major issue.
Criminals can interfere with shipments, alter product labels, or steal goods directly from warehouses and transport vehicles.
Political Instability and Geopolitical Tensions
International conflicts and trade disputes can shut down borders, delay shipments, or limit access to important raw materials.
Supplier Reliability Concerns
Unverified Vendors
Many companies work with suppliers they have never audited. This increases the risk of fraud, poor quality, or unethical practices.
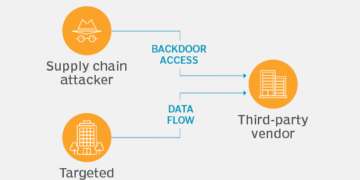
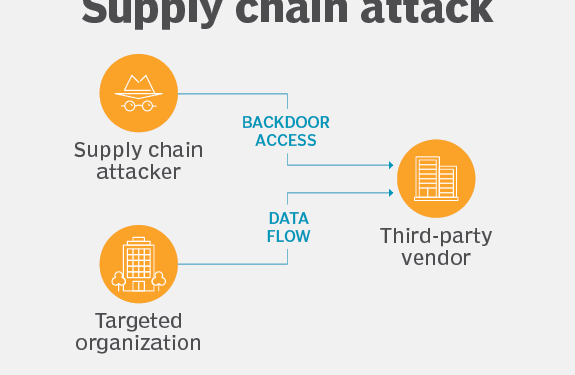
Lack of Transparency in Tier-3 and Tier-4 Suppliers
Businesses often know their direct suppliers but lack visibility into lower-tier vendors. A hidden third-party problem can cause major disruptions.
How Technology Is Transforming Supply Chain Risks
AI and Automation Vulnerabilities
System Manipulation
Hackers can manipulate automated decision-making systems, causing delays or incorrect deliveries.
Algorithmic Bias
AI systems may rely on flawed data, leading to poor forecasting or misjudged supplier performance.
IoT Device Security Weaknesses
Unsecured Sensors
IoT devices frequently used in tracking and monitoring systems can be easy targets if not properly secured.
Supply Chain Tracking Errors
Faulty devices can give inaccurate information about shipment conditions, locations, or security status.
Strategies to Strengthen Supply Chain Security
Enhancing Cybersecurity Measures
Multi-level Monitoring Systems
Companies should use layered defense strategies, including firewalls, intrusion detection, and real-time monitoring.
Employee Cyber Awareness
Human error remains one of the biggest weaknesses. Proper training can significantly reduce risk.
Better Supplier Verification Processes
Supplier Audits
Regular checks ensure vendors follow safety, quality, and ethical standards.
Compliance Checks
Organizations can avoid risk by ensuring all suppliers meet industry regulations.
Leveraging Technology Safely
Encrypted Communication Channels
Encryption protects sensitive information from hackers.
Secure IoT Integration
Using secure, updated devices ensures accurate and safe supply chain tracking.
Conclusion
Supply chain risks are evolving faster than ever. As companies become more interconnected and dependent on technology, the challenges grow. However, by understanding hidden risks and implementing better security strategies, businesses can safeguard their operations, protect customer trust, and stay resilient in a rapidly changing world.